OTP Not Arriving: 12 Common Causes and Platform-Specific Fixes for Gaming, Fintech, and Social Networks
A practical, evidence-driven guide to make one-time passwords actually show up—what breaks, how to fix it (fast), and how to keep accounts reusable across gaming, fintech, and social platforms.
Quick access
TL;DR / Key Takeaways
Make OTP Deliverability Reliable
Fix It Fast, Step by Step
Gaming Platforms: What Usually Breaks
Fintech Apps: When OTPs Are Blocked
Social Networks: Codes That Never Land
Pick the Right Inbox Lifespan
Keep Accounts Reusable
Troubleshoot Like a Pro
The 12 Causes—Mapped to Gaming / Fintech / Social
How-To — Run a Reliable OTP Session
FAQ
Conclusion — The Bottom Line
TL;DR / Key Takeaways
- Most "OTP not received" issues come from resend-window throttling, sender/auth failures, recipient greylisting, or domain blocks.
- Work a structured flow: open inbox → request once → wait 60–90s → single resend → rotate domain → document the fix for next time.
- Select the right inbox lifespan: a quick disposable inbox for speed versus a reusable address (with token) for future re-verification and device checks.
- Spread risk with domain rotation on a reputable inbound backbone; maintain a steady session; avoid hammering the Resend button.
- For fintech, expect stricter filters; have a fallback (app-based or hardware key) ready if email OTP is suppressed.
Make OTP Deliverability Reliable

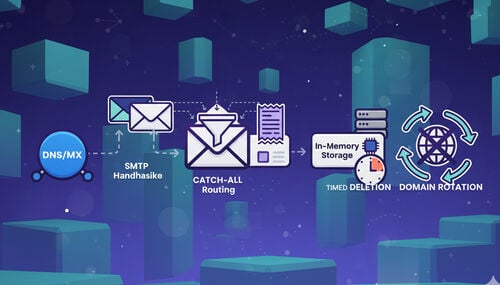
You can start with the inbox behaviors and infrastructure factors that most significantly impact whether code is deployed quickly.
Deliverability begins before you click 'Send code'. Use an inbox that's easy for filters to accept and easy for you to monitor live. A solid primer is the Temp Mail fundamentals—what these inboxes are, how they work, and how messages appear in real-time (see Temp Mail fundamentals). When you need Continuity (e.g., device checks, password resets), reuse your temporary address via a stored token so that platforms recognize the same address across sessions (see 'Reuse Your Temporary Address').
Infrastructure matters. Inbound backbones with a strong reputation (e.g., Google–MX–routed domains) tend to reduce "unknown sender" friction, speed up retries after greylisting, and maintain consistency under load. If you're curious why this helps, read this explainer on why Google-MX matters in inbound processing (see why Google-MX matters).
Two human-side habits make a difference:
- Keep the inbox view open before requesting the OTP, so you can see the arrival instantly rather than having to refresh later.
- Could you respect the resend window? Most platforms suppress multiple rapid requests; a 60–90s pause before the first resend prevents silent drops.
Fix It Fast, Step by Step
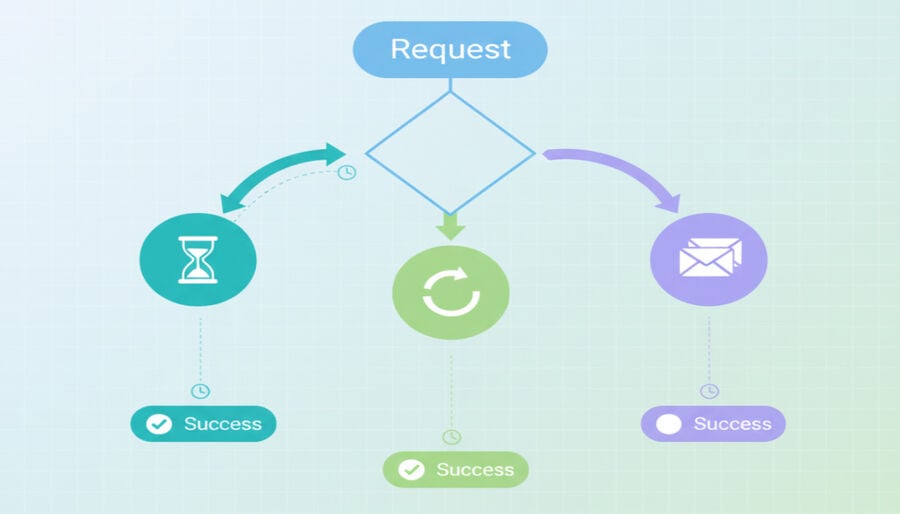
A practical sequence to confirm your address, avoid throttling, and recover a stuck verification.
- Open a live inbox view. Ensure you can view new messages without needing to switch apps or tabs.
- Request once, then wait 60–90 seconds. Don't double-tap Resend; many senders queue or throttle.
- Trigger one structured resend. If nothing arrives after ~90 seconds, press Resend once and monitor the clock.
- Rotate the domain and retry. If both miss, generate a new address on a different domain and try again. A short-lived inbox is fine for quick signups; for now on access, you can use a reusable address with a token (see the short-lived inbox option and use your temporary address).
- Store the token securely. If your inbox supports token-based reopening, save the password in a password manager so you can reverify later with the same address.
- Document what worked. Note the domain that finally passed and the observed arrival profile (e.g., "first attempt 65s, resend 20s").
Gaming Platforms: What Usually Breaks
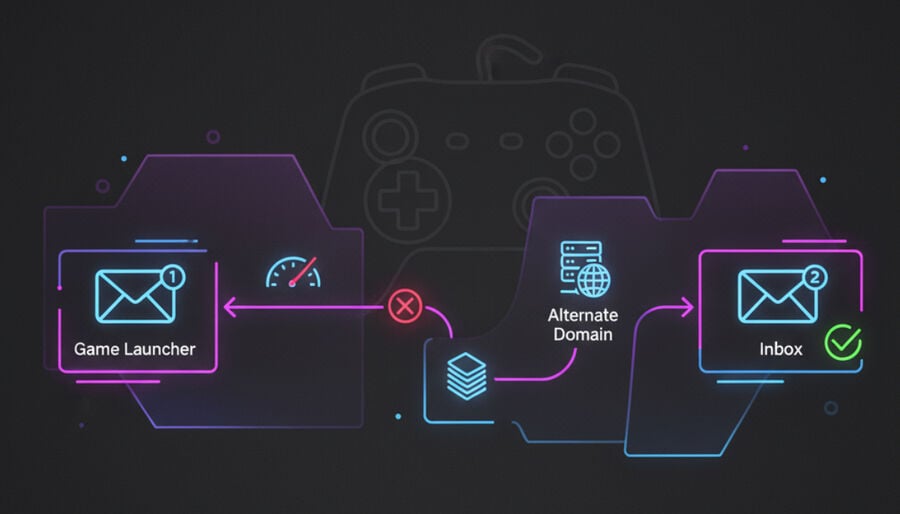
Common fail points with game stores and launchers, plus domain rotation tactics that work.
Gaming OTP failures often cluster around event spikes (such as sales or launches) and strict resend throttles. Typical patterns:
What breaks
- Resend too fast → suppression. Launchers silently ignore duplicate requests within a short window.
- Queueing/backlog. Transactional ESPs can defer messages during peak sales.
- First-seen sender + greylisting. The first delivery attempt is deferred; the retry succeeds, but only if you wait for it to occur.
Fix it here
- Use the one-resend rule. Request once, wait 60–90 seconds, then resend a single time; do not repeatedly click the button.
- Switch to a reputation-strong domain. If the queue feels stuck, rotate to a domain with a better acceptance profile.
- Could you keep the tab active? Some desktop clients do not display notifications until the view is refreshed.
When you need Continuity (device checks, family consoles), capture the token and reuse your temporary address so that future OTPs are sent to a known recipient (see 'Reuse Your Temporary Address').
Fintech Apps: When OTPs Are Blocked

Why banks and wallets often filter temporary domains, and what alternatives you can use safely.
Fintech is the strictest environment. Banks and wallets prioritize low risk and high traceability, so they may filter obvious public temporary domains or penalize rapid resending patterns.
What breaks
- Disposable-domain blocks. Some providers reject signups from public temp domains outright.
- Strict DMARC/alignments. If the sender's authentication fails, recipients may quarantine or reject the message.
- Aggressive rate limiting. Multiple requests within minutes can suppress subsequent sends entirely.
Fix it here
- Start with a compliant address strategy. If a public temporary domain is filtered, consider using a reusable address on a reputable domain, then avoid resending.
- Check other channels. If email OTP is suppressed, see if the app offers an authenticator app or hardware key fallback.
- If you need email, you can use a domain rotation tactic to keep the same user session intact between attempts, thereby retaining risk scoring Continuity.
Social Networks: Codes That Never Land
How resend windows, anti-abuse filters, and session state cause silent failures during signup.
Social platforms fight bots at scale, so they throttle OTPs when your behavior looks automated.
What breaks
- Rapid resends across tabs. Clicking Resend in multiple windows suppresses subsequent messages.
- Promotions/Social tab misplacement. HTML-heavy templates get filtered into non-Primary views.
- Session state loss. Refreshing the page mid-flow invalidates the pending OTP.
Fix it here
- One browser, one tab, one resend. You can keep the original tab active; please don't navigate away until the code lands.
- Could you scan other folders? The code may be in Promotions/Social. Keeping a live inbox view open makes it quickly accessible.
- If the issue persists, rotate domains once and retry the same flow. For future logins, a reusable address eliminates the need to change recipients.
For a hands-on walkthrough, please take a look at this quick start guide for creating and using a temporary address during signup (see the quick start guide).
Pick the Right Inbox Lifespan
Choose between reusable and short-life addresses based on Continuity, resets, and risk tolerance.
Choosing the right inbox type is a strategy call:
table
If you only need a quick code, a short-life inbox option is acceptable (see short-life inbox option). If you expect password resets, device re-checks, or future two-step logins, choose a reusable address and store its token privately (see 'Reuse Your Temporary Address').
Keep Accounts Reusable
Store tokens securely so you can reopen the same inbox for future device checks and resets.
Reusability is your antidote to "I can't get back in." Save the address + token in a password manager. When the app requests a new device check months later, reopen the same inbox, and your OTP will arrive predictably. This practice significantly reduces support time and bounced flows, especially across gaming launchers and social sign-ins that require reverification without notice.
Troubleshoot Like a Pro
Diagnostics for sender reputation, greylisting, and mail-path delays—plus when to switch channels.
Advanced triage focuses on the mail path and your behavior:
- Authentication checks: Poor SPF/DKIM/DMARC alignment on the sender's side often correlates with email being quarantined. If you consistently experience long delays from a specific platform, expect that their ESP is deferring.
- Greylisting signals: First attempt deferred, second attempt accepted—if you waited. Your single, well-timed resend is the unlock.
- Client-side filters: HTML-heavy templates land in Promotions; plain-text OTPs fare better. Keep the inbox view open to avoid missing arrivals.
- When to switch channels: If rotation plus a single resend fails, and you're in fintech, especially, consider pivoting to an authenticator app or hardware key to complete the process.
For a compact playbook focused on OTP arrival behavior and retry windows, see receive OTP codes tips in our knowledge base (see receive OTP codes). When you need broader service constraints (24-hour inbox retention, receive-only, no attachments), please consult the temporary mail FAQ to set expectations before a critical flow (see the temporary mail FAQ).
The 12 Causes—Mapped to Gaming / Fintech / Social
- User typo or copy/paste errors
- Gaming: Long prefixes in launchers; verify exact string.
- Fintech: Must match strictly; aliases may fail.
- Social: Autofill quirks; double-check clipboard.
- Resend-window throttling/rate limiting.
- Gaming: Rapid resends trigger suppression.
- Fintech: Windows longer; 2–5 minutes are common.
- Social: One retry only; then rotate.
- ESP queueing/backlog delays
- Gaming: Sales spikes → delayed transactional mail.
- Fintech: KYC surges stretch queues.
- Social: Signup bursts cause deferrals.
- Greylisting at the receiver
- Gaming: First attempt deferred; retry succeeds.
- Fintech: Security gateways can delay first-seen senders.
- Social: Temporary 4xx, then accept.
- Sender reputation or auth issues (SPF/DKIM/DMARC)
- Gaming: Misaligned subdomains.
- Fintech: Strict DMARC → reject/quarantine.
- Social: Regional sender variance.
- Disposable-domain or provider blocks
- Gaming: Some stores filter public temp domains.
- Fintech: Banks often block disposable accounts completely.
- Social: Mixed tolerance with throttles.
- Inbound infrastructure path problems
- Gaming: Slower MX route adds seconds.
- Fintech: Reputation-strong networks pass faster.
- Social: Google-MX paths often stabilize acceptance.
- Spam/Promotions tab or client-side filtering
- Gaming: Rich HTML templates trip filters.
- Fintech: Plain-text codes arrive more consistently.
- Social: Promotions/Social tabs hide codes.
- Device/app background limitations
- Gaming: Paused apps delay fetch.
- Fintech: Battery saver blocks notifications.
- Social: Background refresh off.
- Network/VPN/corporate firewall interference
- Gaming: Captive portals; DNS filtering.
- Fintech: Enterprise gateways add friction.
- Social: VPN geo affects risk score.
- Clock drift/code lifetime mismatch
- Gaming: Device time off → "invalid" codes.
- Fintech: Ultra-short TTLs punish delays.
- Social: Resend invalidates prior OTP.
- Mailbox visibility/session state
- Gaming: Inbox not visible; arrival missed.
- Fintech: Multi-endpoint viewing helps.
- Social: Page refresh resets flow.
How-To — Run a Reliable OTP Session
A practical step-by-step process for completing OTP verifications using temporary or reusable inboxes on tmailor.com.
Step 1: Prepare a reusable or short-life inbox
Choose based on your goal: one-off → 10-minute mail; Continuity → reuse the same address.
Step 2: Request the code and wait 60–90 seconds
Keep the verification screen open; don't switch to another app tab.
Step 3: Trigger one structured resend
If nothing arrives, tap Resend once, then wait 2–3 more minutes.
Step 4: Rotate domains if signals fail
Try a different receiving domain; if the site resists public pools, switch to a custom domain temporary email.
Step 5: Capture on mobile when possible
Use temporary email addresses or set up a Telegram bot to reduce missed messages.
Step 6: Preserve Continuity for the future
You can save the token so you can reopen the same inbox for resets later.
FAQ
Why do my OTP emails arrive late at night but not during the day?
Peak traffic and sender throttles often cause deliveries to cluster. Could you use the timing discipline and send it one more time?
How many times should I tap "Resend" before switching domains?
Once. If still nothing after 2–3 minutes, rotate domains and re-request.
Are disposable inboxes reliable for bank or exchange verifications?
Fintechs can be stricter with public domains. Use a custom domain temp inbox for the verification phase.
What's the safest way to reuse a disposable address months later?
Could you store the token so you can reopen the same inbox for re-verification?
Will a 10-minute inbox expire before my OTP arrives?
Usually not if you follow the wait/resend rhythm; for resets later, choose a reusable inbox.
Does opening another app cancel my OTP flow?
Sometimes. Keep the verification screen in focus until the code arrives.
Do you know if I can receive OTPs on my mobile and paste them on my desktop?
Yes—set a temporary email on your mobile device so you don't miss the window.
What if a site blocks disposable domains entirely?
Rotate domains first. If you are still blocked, use a custom domain temporary email.
How long do messages remain visible in a temp inbox?
Content typically remains visible for a limited retention window; you should plan to act quickly.
Do large MX providers help with speed?
Reputation-strong routes often surface emails more quickly and consistently.
Conclusion — The Bottom Line
If OTPs aren't arriving, don't panic or spam "Resend." Apply the 60–90 second window, single resend, and domain rotation. Stabilize device/network signals. For stricter sites, shift to a custom domain route; for Continuity, reuse the same inbox with its token—especially for re-verification months later. Capture on mobile so you're never out of reach when a code drops.